VPC VPN DX
| Owner | |
|---|---|
| Verification | |
| Tags | |
| Last edited time |
VPC
- Up to 5 per region (soft limit), up to 5 CIDR per VPC (min /28 = 16 -max /16 = 65K)🦍Can expand after creation with up to 4 secondary IPv4 IP ranges (CIDRs) to it.
- Only private IPv4 = 10.0.0.0 / 172.16.0.0 / 192.168.0.0 No overlapping
- 5 address are reserved by AWS : 0 network, 1 router 2 DNS, 3 TBD, 255 broadcast
- Bastion Host Connecting to a private instance from a dedicated public host that allows SSH access throw it AZ specific, uses an Elastic IP, requires an IGW,
- Internet gateway 5 - 45 Gbps auto scaling, no ports to manage.
- Security Groups & NACLs:
- NACL = stateless Firewall at the subnet level (in rule + our role), 1 per subnet, hierarchy roles, deny if no role (Default NACL is created for every account that allows all in out traffic)
- Security group = stateful FW at the ENI level (one rule , only allow rules ) an EC2 Instance can have multiple Security Groups
- Ephemeral Ports Connecting two endpoints (clients connect to servers) the reply from the server comes back to the client (win 10 - 49152) (Linux 32768 - 60999)
- Traffic Mirroring to an EC2 in order to mirror and analyze network traffic
(In AWS: need to configure NACL with same port ranges )
VPC Endpoints
Allows to connect to AWS services within the private network
VPC Gateway Endpoint - for S3, Dynamo - need DNS resolution in the VPC
- specify
AWS:sourceVpceas a condition in the bucket policy
VPC Interface Endpoint - for Other AWS Services (creates a private ENI) use Security Group
- need to enable DNS hostname and DNS support in the VPC
- can be accessed from DX and VPN
Endpoint Policys
JSON policy - allows to control access using the Endpoint
NAT Gateway
A NAT gateway is a service that allows instances in a private subnet to connect to external services while preventing external services from connecting to the instances, by replacing the source IPv4 address with its private IP before sending traffic and reversing the process when sending response traffic. When you create a NAT gateway, you specify one of the following connectivity types:
Public – (Default) IA public NAT gateway can be used to connect instances in private subnets to the internet, other VPCs, or an on-premises network, and must be associated with an elastic IP address at creation. Traffic is routed from the NAT gateway to the internet gateway for the VPC, or through a transit gateway or virtual private gateway for other connections.
Private – Private subnets in a VPC can connect to other VPCs or an on-premises network through a private NAT gateway, but traffic routed from the NAT gateway to an internet gateway will be dropped.
NAT Instance – When a connection times out, a NAT instance sends a FIN packet to close the connection with any resources behind it.
NAT Gateway – When a connection times out, a NAT gateway sends an RST packet to any resources behind the NAT gateway that attempt to continue the connection, instead of sending a FIN packet.
NAT Gateway
A NAT gateway enables private subnet instances to connect to external services while preventing those services from connecting to the instances. It does this by replacing the source IPv4 address with the instance's private IP and then reversing the process when sending response traffic. There are four types of NAT gateways, each specified by their connectivity type:
- Public: Used to connect instances in private subnets to the internet, other VPCs, or an on-premises network. It must be associated with an elastic IP address at creation. Traffic is routed from the NAT gateway to the internet gateway for the VPC or through a transit gateway or virtual private gateway for other connections.
- Private: Private subnets can connect to other VPCs or an on-premises network through a private NAT gateway. However, any traffic routed from the NAT gateway to an internet gateway will be dropped.
- NAT Instance: When a connection times out, a NAT instance sends a FIN packet to close the connection with any resources behind it.
- NAT Gateway: When a connection times out, a NAT gateway sends an RST packet to any resources behind it that attempt to continue the connection, instead of sending a FIN packet.
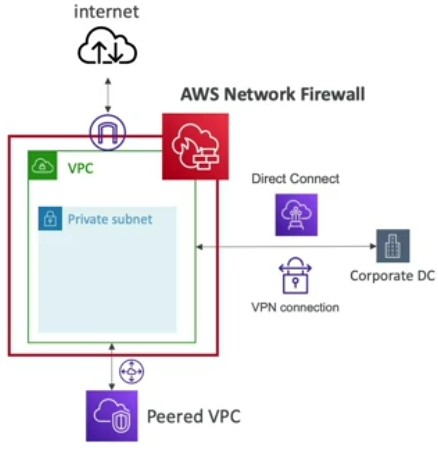
AWS Netwrok Firewall
Protects the entire VPC and covers all connections using Rules, filters protocols
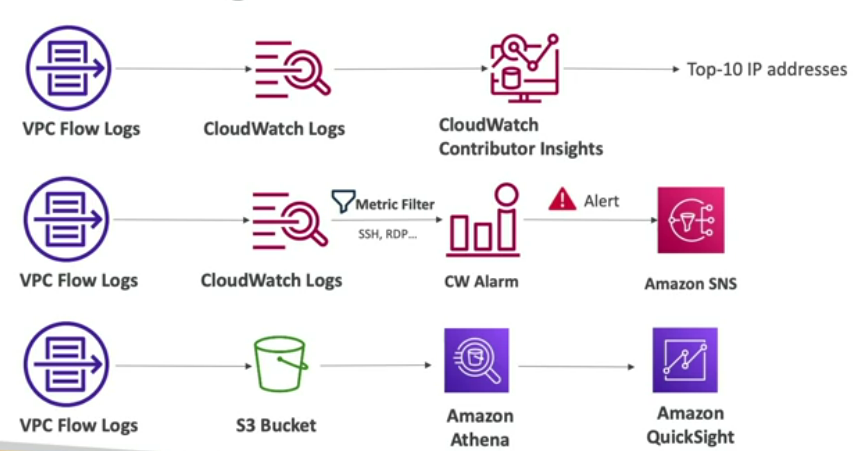
VPC Flow Logs
Inbound Reject = NACL or SG
Inbound Accepted - Outbound Rejected = NACL (SG ALLOWS ALL OUT BY DEFAULT)
VPC Routing
Every VPC has a main route table that is associated with all subnets
can create a private route table to every subnet
VPC Web Proxy
Companies can use AWS VPN/Direct Connect or build a proxy farm with Squid and ELB to improve performance, filter URLs, monitor security, and protect against threats. A web proxy like Squid can limit outbound web connections from a VPC and be scaled, highly available, and automated with whitelists or DNS filtering.